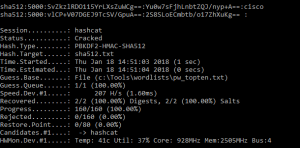
I haven’t seen too much detail around about how to crack Cisco ASA PBKDF2 (Password-Based Key Derivation Function 2) SHA-512 hashes, which I believe have been supported in some ASA versions from as early as March 2016. As always the hashes can be recovered from the appropriate Cisco ASA config file. Here are some examples of how …
Category: Passwords
Jun 26
Kerberos Username Enumeration – Top 500 Common Usernames
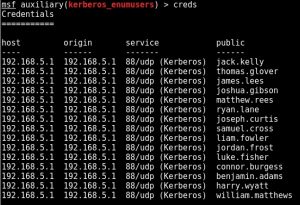
Kerberos Username Enumeration – Username Wordlists I’ve been having a fair bit of joy with the auxiliary/gather/kerberos_enumusers metasploit module on internal engagements, however you do need to provide the module with a good quality username wordlist or wordlists. On a recent engagement, using only the top 50 male and female userlists, I was able to guess 70 …