Nmap-ssl-parser
Nessus and Nmap both do a decent job of enumerating supported SSL protocols and ciphers from remote servers. However, I usually find myself also utilising other 3rd party SSL scanning tools. To that end I wanted an easy way to quickly parse out SSL services to an output file for input into other tools.
Nmap-ssl-parser is a python script designed to query nmap XML output and provide a list of usable ssl services in the format host:port
The nmap-ssl-parser script parses an nmap.xml output file, extracts all SSL services and writes them to a filename of your choice.
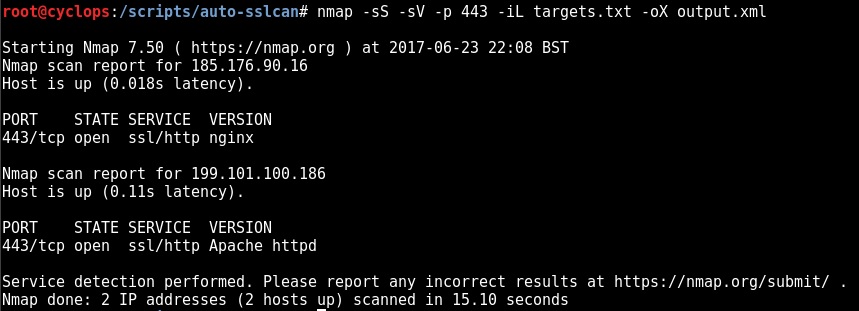
Step 1 – Create a valid nmap .xml file:
Note: Some form of Nmap version scanning must be utilised to create the XML ouput i.e. -sV or -A (In order to determine whether the service is SSL enabled)
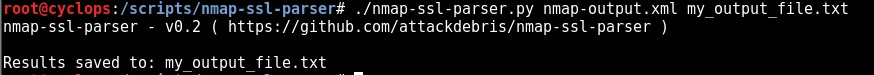
Step 2 – Parse the nmap .xml file with nmap-ssl-parser.py:
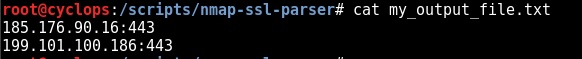
That’s effectively job done, as can be seen below our output file “my_output_file.txt” contains our host:port formatted list ready for importing into any other tool of choice:
The code and installation instructions can be found here: https://github.com/attackdebris/nmap-ssl-parser
Also check out auto-sslscan, which takes this process a step further by automating sslscans from the parsed list of SSL services: https://github.com/attackdebris/auto-sslscan
Credit – The base code I used to create nmap-ssl-parser: https://github.com/DanMcInerney/nmap-parser/blob/master/nmap-parser.py