Auto-sslscan
As I mentioned in the previous post whilst Nessus and Nmap do a reasonable job of enumerating SSL protocols and ciphers I often find myself utilising other 3rd party SSL scanning tools. One I find myself turning to on a regular basis is sslscan, I like the output it provides and issues become immediately apparent, although if you prefer using SSL scanning tool X or Y, the auto-sslscan code can be easily amended to cater for your tool of choice.
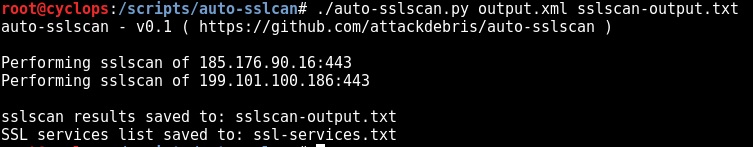
Auto-sslscan is a python script designed to automate the process of conducting ssl scanning via sslcan. The Auto-sslscan script parses an nmap.xml output file, extracts all SSL services and automatically performs an sslscan of them.
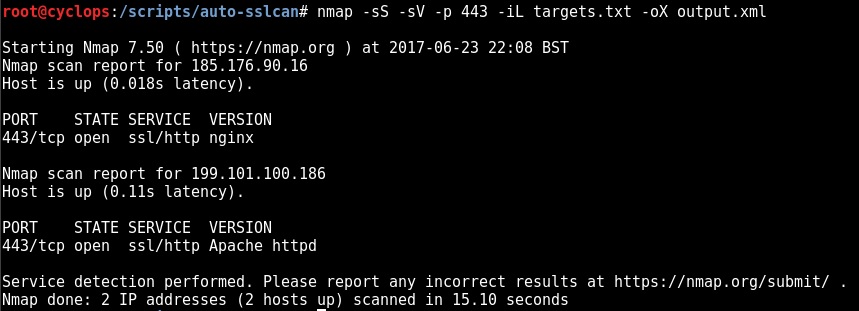
Step 1 – Create a valid nmap .xml file:
Note: Some form of Nmap version scanning must be utilised to create the XML ouput i.e. -sV or -A (In order to determine whether the service is SSL enabled)
Step 2 – Process the Nmap XML file with auto-sslscan.py:
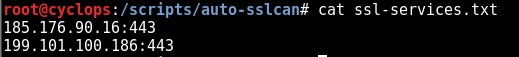
SSL Services:
That’s effectively job done, we now have a list of SSL services if we wish to target them again with another tool:
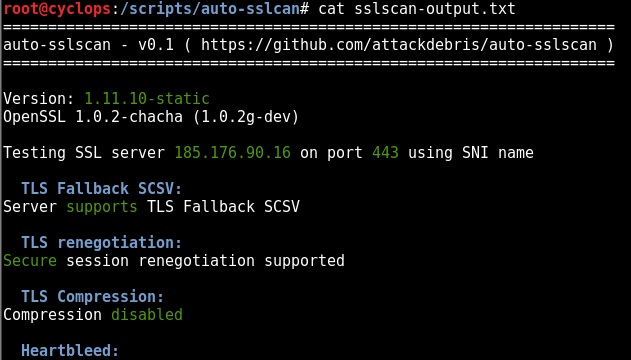
SSL Scan Ouput:
The actual SSL scanning “sslscan” ouput is saved to a concatenated file (truncated image below):
The code and installation instructions can be found here: https://github.com/attackdebris/auto-sslscan
Also check out nmap-ssl-parser, which simply parses the nmap XML file and provides a list of SSL services: https://github.com/attackdebris/nmap-ssl-parser
Credit – The base code I used to create nmap-ssl-parser: https://github.com/DanMcInerney/nmap-parser/blob/master/nmap-parser.py